What is CryptoLocker?
There are many security risks to worry about when managing or using a business network. However, one of the biggest threats to a business' network is Malware. There are many different forms of malware that can infect systems in an unlimited number of ways. Recently, our techs at DCS have encountered many computers infected with CryptoLocker – a new form of Ransomware (a form of malware that will be explained later in this blog post) that is proving to be a major problem for numerous businesses.
In order to avoid CryptoLocker, it is recommended that all Windows users understand what CryptoLocker is, what ransomware is, as well as how you can take steps to protect your network from malware such as CryptoLocker and other ransomware.
What is CryptoLocker?
CryptoLocker is a nasty ransomware trojan which disguises itself in many different forms and can infect any Windows computer. Once a computer is infected with CryptoLocker, the trojan begins locking files and demands payment from the user if they want to recover their files.
What is ransomware?
Ransomware is a type of malware that encrypts important files and requests that users pay a "ransom" to regain access to them. Ransomware is not a new type of malware, but it has become increasingly prevalent in recent months because of CryptoLocker and other ransomware variations such as CryptoWall.
How does CryptoLocker spread?
CryptoLocker has been shown to spread in four different ways:
- As an email sent to company addresses pretending to be from customer support from FedEx, UPS, DHL, etc. The trojan is attached to the email, usually labeled as a tracking number.
- In PDF documents that are attached to emails, often labeled "My Resume" or "Resume".
- Through hacked websites that can exploit computer vulnerabilities to install the malware.
- Through trojans that pretend to be applications you need to download in order to watch videos online
CryptoLocker installs itself to the Documents and Settings folder on your computer and then proceeds to search for specific types of files that often store information that is important to a user, like Microsoft Word Docs or Adobe PDFs. CryptoLocker applies an asymmetric encryption which requires both a public and private key to unlock. The public key is stored in the malware itself and is used to encrypt the files. The private key, the key that is being sold by the hacker, is hosted on the hacker's personal server.
What happens if my computer becomes infected?
If your system is infected, your files will be encrypted and a pop-up message will appear, informing you that your files have been encrypted and that in order to get the key to unlock them (the private key), you'll need to pay up to USD$300, or a similar amount in another currency. We have notices that the demanded ransom tends to change between different CryptoLocker infections and has increased, with older versions asking for USD$100.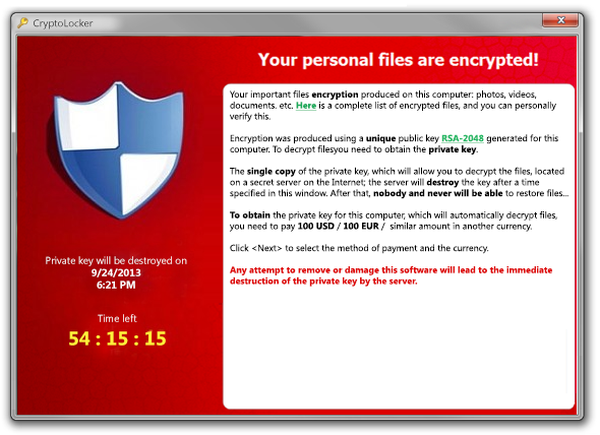
You may also see a timer counting down from 100 hours. If this reaches zero, your encrypted files will be deleted with a very small chance of your data being recoverable. The preferred method of payment is in BitCoins – an anonymous digital cryptocurrency. The pop-up window which informs you of your infection and the ransom will have instructions on how to send the payment – usually through an online payment service like Green Dot – MoneyPak.
Luckily, once you send the ransom, you will be sent the private key which will allow you to unlock your files. The hackers have stated that they won’t re-infect computers which have paid the ransom, and network security companies have confirmed that, so far, this has been true.
Although most recently-updated antivirus and antimalware software will detect a CryptoLocker infection, most will be unable to recover or decrypt files even if the malware itself is deleted. If you see the CryptoLocker pop-up window, it is too late to rid your computer of the trojan. However, this does not mean that is impossible to recover your files.
How can I recover my data without paying the ransom?
If you or your IT professional has made a backup of your system prior to the infection, it is possible to do a full reinstall of Windows and restore your files from the backup. However, if a backup was made after CryptoLocker had already found its way into your filesystem, then it is much less likely that your files can be recovered without paying the hackers.
How do I prevent CryptoLocker from infecting computers on my network?
This is a serious piece of malware that should not be taken lightly. If you are worried about your network's computers becoming infected, here are five steps you can take to prevent infection from occurring:
- Be proactive – It is a good idea to educate yourself and your staff about ransomware, specifically CryptoLocker, and even implement and reinforce a "no installing programs without administrator approval" rule. Also, having a functional and redundant backup plan in place will go a long way in limiting the damage CryptoLocker can do.
- Check your emails carefully – Closely look at every email that comes into your inbox. Pay close attention to who sent it, the body text and even the subject line. If you see a slight spelling error in the name or even in the address e.g., [email protected], you should immediately delete the email.
- Beware of attachments – Always look carefully at attachments you receive, even if they appear trustworthy. If you get an email with an attachment from any sender you don’t personally know, don’t open it. If you get an attachment from people you do know, but it isn’t something they would normally send, don’t open it. For all other attachments, try confirming that the file attached is in fact legitimate by asking the sender.
- Backup your data – Be sure to always backup your data on a regular basis. If you backup files on a daily or even weekly basis and are infected, you can easily wipe your hard drive and start again without losing much in the way of data.
- Know what to do if infected – If you are infected the first thing you should do is disconnect from the network to limit the chance of the virus spreading to other systems. If you have backed up your system and data, you can probably revert your system. If not, your best plan of attack would be to contact us to see if we can help, as we may be able to get around the encryption or even delete it.